While almost everyone who uses computers is aware of the prevalence of viruses, far fewer are aware of Phishing, a technique used by cybercriminals to obtain sensitive information and access. While viruses operate by secretly installing software that corrupts a computer’s operating system, Phishing schemes rely on social engineering to get results. Social engineering, simply put, is manipulating a person to do something they may not do otherwise – in the case of Phishing, divulging sensitive or confidential information. Let’s take a closer look at Phishing and how it’s used, how common it is, and what to do to avoid it.
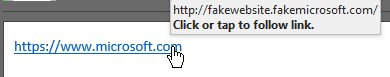
The term “Phishing” originates as a homonym of “fishing,” as the concept is similar: throw out some bait and hope to catch something. In Phishing, this bait usually comes in the form of email or phony websites. These emails and websites will attempt to look legitimate, usually requesting login credentials or financial information, typically under the guise of needing the information to maintain an account or receive/authorize funds. Phishing emails can often be well-composed, appearing to come from the company or organization they purport to be (although more obvious Phishing attempts will often be riddled with spelling/grammar errors). These emails will often link to a website where the action item is requested, and these sites can also be fairly convincing, using official logos and layouts reminiscent of their legitimate counterparts. These links can sometimes be multi-purpose: they will both collect sensitive information, as well as infect a computer with a virus or malware that collects even more information and further compromises an individual. One can check the legitimacy of a link by hovering the mouse cursor over it: doing so will reveal the true destination of the link, which can be easily misrepresented in the email body.
A “Microsoft” link that does not go to a real Microsoft site is probably not valid!
A more advanced form of Phishing is called “Spear Phishing,” in which a specific individual or group of individuals at a specific organization are targeted. These require more research on behalf of the cybercriminal, who will have to determine how to best fool their target. For example, CFOs are often targeted with requests that appear to come from other members of the executive team, requesting urgent wire transfers of large sums of cash. It is trivially easy for an attacker to “spoof” an email address, so that the email appears it comes directly from the fellow employee. Another common technique is for an attacker to pretend to be a member of the IT department, who will then request credentials from a person of authority so that they can access the network and obtain sensitive information, and perhaps install software that collects more of this information over time.
Kaspersky Lab, a provider of anti-virus software, holds roughly 3% to 5% of the anti-virus market share. In Q1 2016, the Anti-Phishing system included with Kaspersky was triggered nearly 35 million times!* Keep in mind, these are emails that were flagged immediately as Phishing attempts, so it does not include those that got through unnoticed, and Kaspersky’s data only represents, at most, 5% of PC users. Extrapolating the data roughly, you can see there are billions of Phishing attempts annually. Because of this, it is vital to have employees be aware of Phishing techniques and the appropriate course of action to take when questioning the legitimacy of an email.
When reading an email that requests any sort of action on behalf of the recipient, employees should carefully consider whether the request seems legitimate. Microsoft and Apple, for example, will never email an individual to request credentials, for any reason. Banking and other financial institutions will never request account passwords or other sensitive details via email either. While some Phishing attempts will come from legitimate looking email addresses, many come from garbage email addresses that should flag a user’s attention immediately (for example, an “Apple” email coming from something like [email protected]).
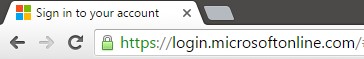
Of course, from time to time it is necessary to enter sensitive information into websites, and this is another time it is vital to be vigilant. When logging in or signing up for a service online that requires personal or financial information, these sites should be secure. How can you tell if a site is secure? Security Certificates are issued to companies to verify their identity and that the information being entered is encrypted in transit, so that hackers cannot steal the information. These websites will start https:// (as opposed to http://), the ‘s’ standing for “secure”. They will also be preceded by a green icon that shows a site has a valid certificate:
If your browser warns that a website’s certificate is invalid, it’s a clear sign that the site is not legitimate.
By being aware of the prevalence of Phishing emails, the techniques used, and the steps to avoid being “caught”, your employees can be better protected, which in turn keeps your company protected. Employees should not hesitate to contact their IT department or provider when a questionable email comes in. IT professionals are well-trained to spot Phishing emails and analyze the technical details of email headers to determine the legitimacy of any email. For an IT person, taking a minute to look at a questionable email is far preferable to spending hours mitigating a poor decision. To learn more about Phishing, network security, and general IT support, contact us today.
*https://securelist.com/analysis/quarterly-spam-reports/74682/spam-and-phishing-in-q1-2016/